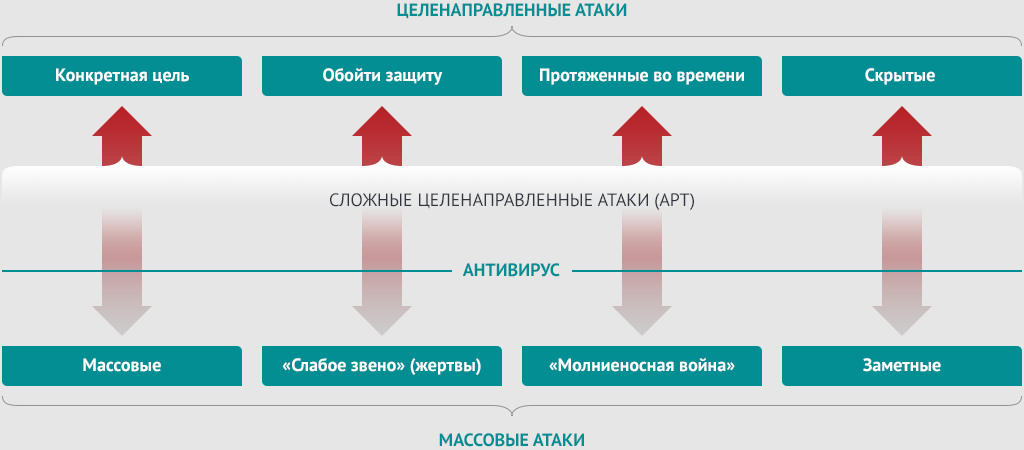
Целенаправленная атака отличается от массовой следующими характеристиками:
- Наличие заказа
- Конкретная цель атаки
- Адаптивность и протяженность во времени
- Скрытость атаки
InfoWatch Targeted Attack Detector
Решение InfoWatch Targeted Attack Detector основано на технологии динамического обнаружения атак.
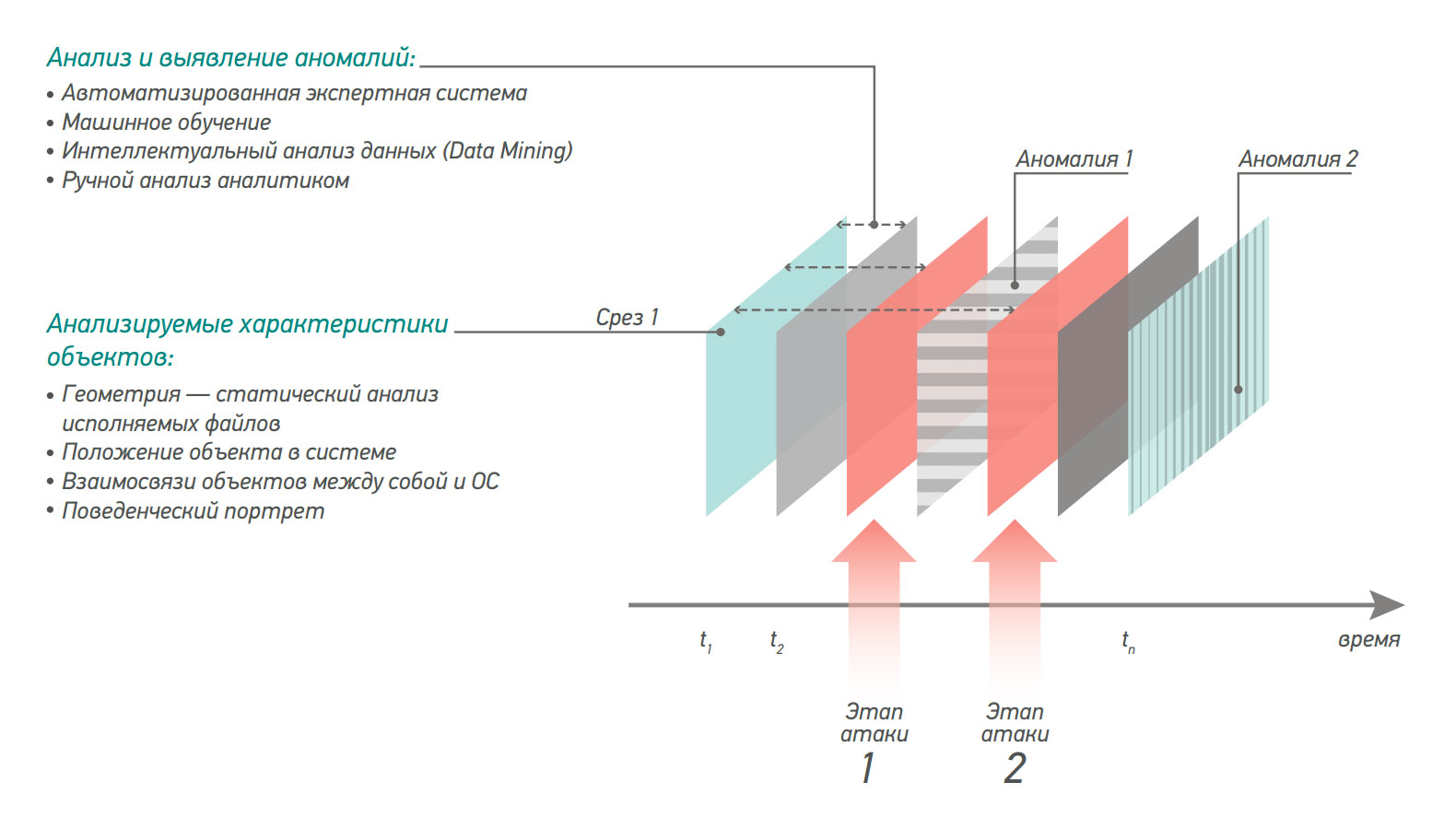
На каждом из компьютеров, составляющих ИТ-инфраструктуру, периодически выполняются сканирования с целью сбора и классификации широкого спектра характеристик объектов системы. Результатом сканирования является срез системы (slice), который подвергается нескольким видам анализа:
Статический
анализ
Классификация всех объектов, входящих в срез системы. Используются такие методы, как классификаторы («decision tree»), «белые списки» (whitelisting), анти-руткит технологии, механизмы выявления похожих объектов («задача k-ближайших соседей»). С помощью статического анализа выявляются объекты, обладающие нетипичными характеристиками.
Динамический анализ —
основа решения
Целью данного вида анализа является выявление изменений и поиск в этих изменениях аномалий. Для определения того, какие срезы сравнивать между собой, используется алгоритм, учитывающий динамику во времени, возникновение критических событий в системе, внешние изменения.
Анализ аномалий
Для определения причин появления аномалий в решении InfoWatch Targeted Attack Detector используется уникальная Экспертная система и ряд метаклассификаторов, оперирующих результатами работы других анализаторов (статического и динамического). При обнаружении неизвестного вредоносного ПО для предоставления в отчете подробного описания его действий и последствий работы для инфраструктуры предприятия привлекается аналитик компании InfoWatch.
АРХИТЕКТУРА РЕШЕНИЯ
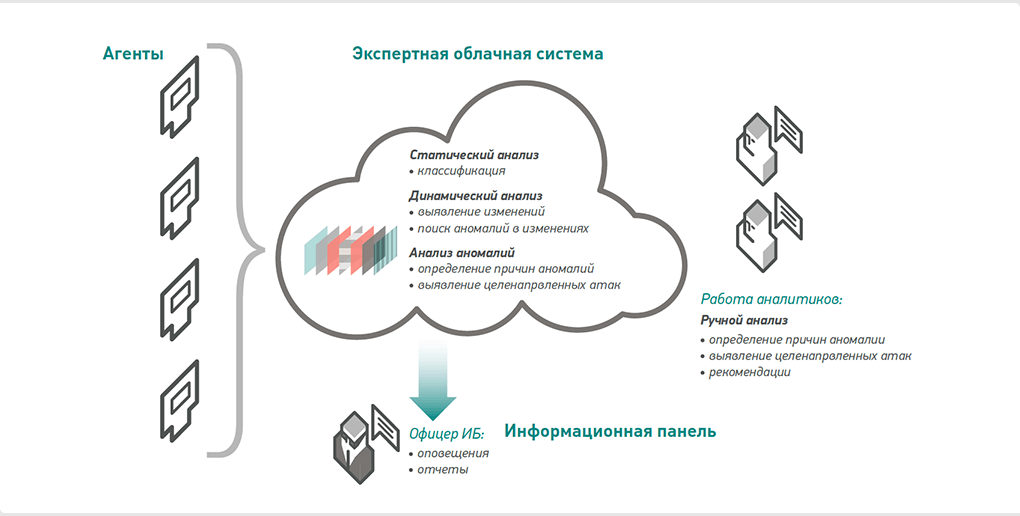
Агент
На каждый из защищаемых компьютеров устанавливается агент, который выполняет периодическое сканирование состояния системы. Результатом каждого такого сканирования является срез системы (slice), который состоит из более 200 свойств объектов, их характеристик и взаимосвязей. Эта информация передается в Автоматизированную Экспертную Систему.
Автоматизированная
Экспертная Система
Уникальная облачная система для анализа больших массивов данных Big Data. Система предназначена для классификации программного обеспечения, поиска вредоносного ПО и выявления целенаправленных атак или их следов.
Информационная web-консоль
Oфицер информационной безопасности или системный администратор могут самостоятельно получить доступ к параметрам работы решения InfoWatch Targeted Attack Detector: статистике по работе агентов, сканирований, найденных объектов, новых, подозрительных и вредоносных объектов.
ПРЕИМУЩЕСТВА РЕШЕНИЯ
- Эффективная защита ценной информации, снижение репутационных и финансовых рисков
- Уникальный подход и передовые технологии
- Простота внедрения и использования
- Наглядные отчеты и экспертное заключение
Данное решение совместно с DLP-системой InfoWatch Traffic Monitor составляет уникальный комплекс защиты ценной для бизнеса информации, позволяющий анализировать все информационные потоки, включая те, что формируются принудительно, вследствие действий вредоносного ПО.
При этом InfoWatch Targeted Attack Detector позволит выявить ПО, направленное на обход или блокировку работы DLP-системы, тем самым обеспечив защиту решения и непрерывность бизнес-процессов компании.
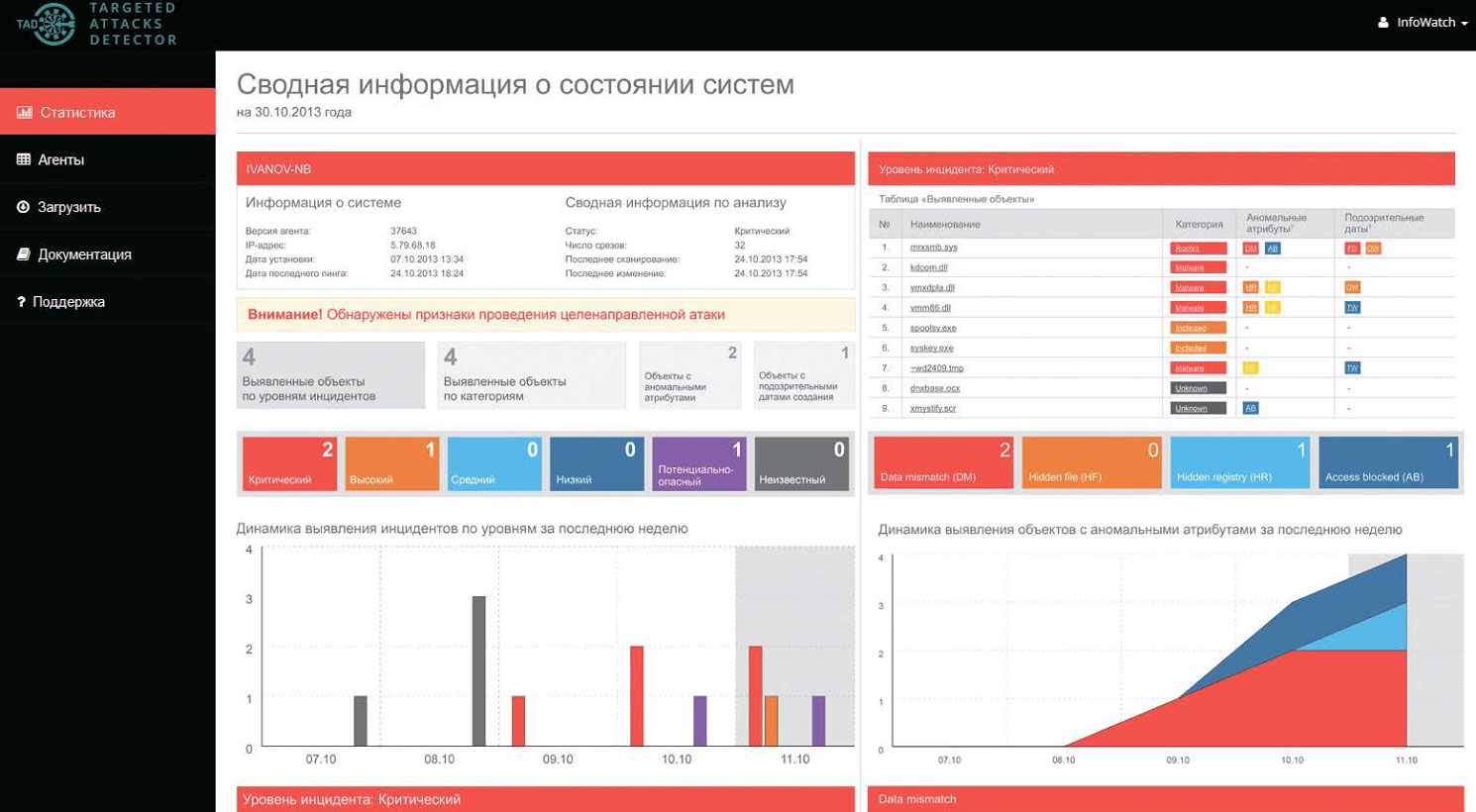
Как это работает?
Скриншот
web-консоли
Документацию по решению можно посмотреть здесь
Заказать обратный звонок
Пожалуйста, заполните форму и мы свяжемся с Вами



